Introduction
In today’s digital age, network security is a critical concern for modern enterprises. Unified Threat Management (UTM) firewalls have emerged as a comprehensive solution to address diverse security challenges. This article delves into the significance in enhancing enterprise security, exploring their key features, working mechanisms, benefits, and limitations. We will also provide insights into selecting the right UTM firewall and discuss best practices for implementation. Lastly, we will touch upon future trends in UTM firewalls, emphasizing their evolving role in safeguarding IT infrastructure.
What is a UTM Firewall?
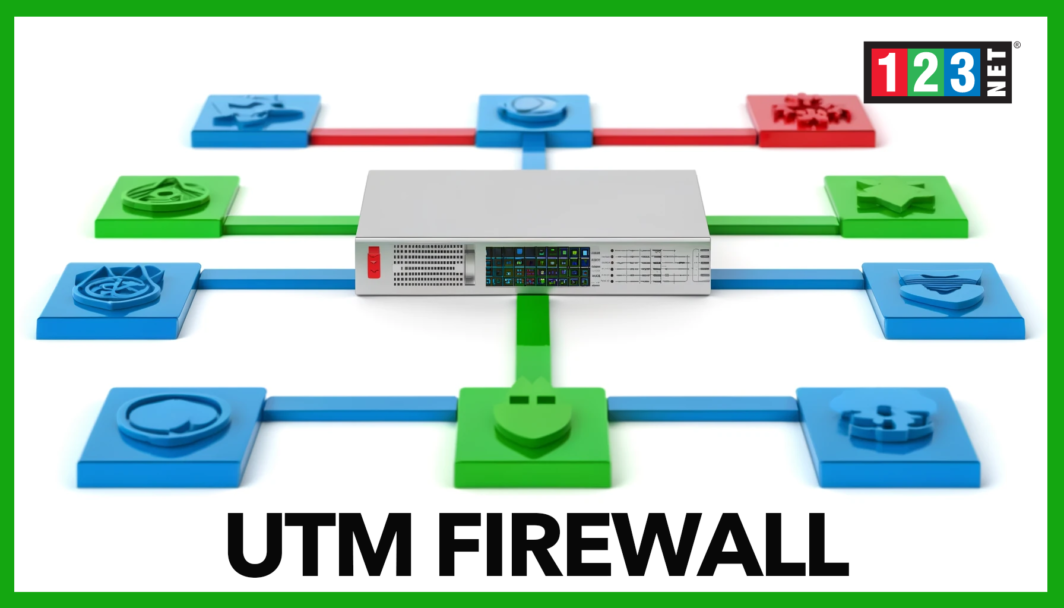
Unified Threat Management (UTM) refers to a comprehensive security solution that integrates multiple protective features into a single, cohesive appliance. This approach contrasts with traditional firewalls, which focus primarily on monitoring and controlling network traffic based on predetermined rules. UTM firewalls enhance traditional capabilities by incorporating advanced functions such as intrusion detection and prevention, anti-virus, anti-malware, web filtering, and email security.
A UTM firewall’s holistic approach to threat management means it can provide a more robust defense against a wide range of cyber threats. Intrusion detection and prevention systems (IDPS) can identify and mitigate unauthorized access attempts and malicious activities in real time. Anti-virus and anti-malware components ensure that malicious software is detected and neutralized before it can cause harm. Web filtering capabilities block access to dangerous or inappropriate websites, protecting users from phishing and other web-based threats.
Email security within helps to safeguard against phishing attacks, spam, and email-borne malware, ensuring that communications remain secure. Application control features allow administrators to manage and restrict the use of specific applications, reducing the risk of unauthorized access or data leakage. Additionally, they often support Virtual Private Network (VPN) configurations, enabling secure remote access to the network.
By combining these diverse security functions into a single solution, it simplifies network security management, reduce the need for multiple security appliances, and provide a comprehensive defense against the ever-evolving landscape of cyber threats. This makes it an essential component in modern enterprise cybersecurity strategies, offering enhanced protection and streamlined security operations.
Key Features of UTM Firewalls
UTM firewalls are equipped with various features that significantly enhance network security. These features work in unison to provide a comprehensive security solution for enterprises.
Intrusion Detection and Prevention
Intrusion Detection and Prevention Systems (IDPS) are a crucial component of UTM firewalls. They identify and mitigate unauthorized access attempts and malicious activities by monitoring network traffic for suspicious behavior. When a potential threat is detected, the system can automatically take action to block or neutralize the threat, ensuring that the network remains secure.
Anti-virus and Anti-malware
UTM firewalls offer robust anti-virus and anti-malware protection, providing real-time defense against a wide range of malicious software. This feature scans incoming data for known viruses and malware, promptly removing or quarantining any detected threats to prevent them from compromising the network.
Web Filtering
Web filtering is another vital feature that it blocks access to malicious or inappropriate websites, protecting users from phishing attempts and other web-based threats. By controlling the websites that users can visit, web filtering helps maintain a safe browsing environment and reduces the risk of cyber attacks originating from harmful sites.
Email Security
Email security features within UTM firewalls protect against phishing, spam, and email-borne threats. This includes scanning incoming and outgoing emails for malicious content, blocking suspicious emails, and ensuring that sensitive information is not transmitted via unsecured channels.
Application Control
Application control allows administrators to manage and restrict access to specific applications. This feature prevents unauthorized usage and helps enforce organizational policies regarding application use. By controlling application access, enterprises can reduce the risk of data breaches and ensure that only approved applications are used within the network.
VPN Support
UTM firewalls often include support for Virtual Private Networks (VPNs), which ensure secure remote access to the network. VPNs encrypt data transmitted between remote users and the network, providing a secure communication channel that protects sensitive information from being intercepted.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) features within UTM firewalls help prevent sensitive data from being leaked or stolen. DLP systems monitor and control the flow of data within the network, ensuring that confidential information is not transmitted outside authorized channels. This feature is essential for maintaining data integrity and compliance with regulatory requirements.
How UTM Firewalls Work
UTM firewalls function by inspecting network packets and monitoring traffic in real time, ensuring robust security across the network. The packet inspection process involves analyzing each data packet to detect potential threats or suspicious activities. They employ advanced algorithms and signature-based detection techniques to swiftly identify and respond to threats.
Packet inspection is a critical component of UTM firewalls. It involves deep packet inspection (DPI), which goes beyond basic header information to examine the actual data content within the packets. This thorough analysis helps identify known threats and anomalous behavior that may indicate new or evolving threats. Signature-based detection compares packet data against a database of known threat signatures, enabling the UTM firewall to recognize and mitigate threats quickly.
Real-time threat monitoring is another essential feature of UTM firewalls. By continuously monitoring network traffic, UTM firewalls can detect and respond to threats as they occur. This immediate action is crucial for preventing cyber threats from compromising the network. Real-time monitoring also allows for dynamic adjustments to security policies, ensuring that the firewall adapts to new threats and maintains optimal protection.
In addition to packet inspection and real-time monitoring, UTM firewalls provide comprehensive threat management through integrated features such as intrusion detection and prevention, anti-virus and anti-malware protection, web filtering, and more. By combining these capabilities, UTM firewalls offer a holistic approach to network security, providing continuous protection against a wide range of cyber threats and ensuring the integrity and safety of the enterprise’s digital assets.
Benefits of Using UTM Firewalls
UTM firewalls provide a range of advantages for enterprises, enhancing their network security and overall operational efficiency.
Comprehensive Security Solution
UTM firewalls deliver an all-in-one protection against a myriad of threats. By integrating multiple security features such as intrusion detection, anti-virus, anti-malware, web filtering, and email security into a single appliance, It offers a holistic approach to network security. This comprehensive coverage ensures that enterprises are protected from a wide range of cyber threats, simplifying the security architecture and reducing potential vulnerabilities.
Simplified Management
One of the key benefits of UTM firewalls is the centralized management interface they provide. This interface streamlines security operations by allowing administrators to manage all security features from a single dashboard. Simplified management reduces the complexity of overseeing various security tools, making it easier to implement and enforce security policies, monitor network traffic, and respond to incidents promptly.
Cost-Effectiveness
UTM firewalls are cost-effective because they reduce the need for multiple security appliances. By consolidating various security functions into one device, organizations can lower their overall hardware and software costs. Additionally, the simplified management reduces the need for extensive administrative resources, further contributing to cost savings.
Scalability and Flexibility
As organizations grow, their security needs evolve. UTM firewalls offer scalability and flexibility, allowing enterprises to easily expand their security infrastructure. Whether it’s adding new features or accommodating increased network traffic, it can adapt to the changing requirements of the organization, ensuring continued protection without significant additional investment.
Enhanced Compliance with Regulatory Requirements
Compliance with regulatory standards is critical for many enterprises. UTM firewalls assist in meeting these requirements by providing robust security features that align with industry standards and regulations. Features such as data loss prevention (DLP), encryption, and detailed logging and reporting capabilities help organizations maintain compliance. As well as avoid penalties, and protect sensitive data.
Challenges and Limitations of UTM Firewalls
Despite their numerous benefits, UTM firewalls present several challenges:
Performance Issues under Heavy Load
One significant limitation of UTM firewalls is their performance under heavy load. When handling high volumes of network traffic, it may experience reduced performance, leading to slower processing speeds and potential network bottlenecks. This can affect the overall efficiency of the network and the user experience, especially in large organizations with substantial data flow.
Complexity in Configuration and Management
UTM firewalls require skilled personnel for proper setup and maintenance. The complexity of configuring and managing multiple integrated security features can be daunting. Incorrect configuration can lead to security gaps, making the network vulnerable to attacks. Additionally, ongoing management and regular updates demand expertise to ensure that the firewall continues to operate effectively and securely.
Potential for Single Point of Failure
UTM firewalls can become a single point of failure within a network. If it encounters an issue or fails, it can leave the entire network vulnerable to cyber threats. This dependency on a single security device underscores the importance of having a robust failover and redundancy plan. This is to mitigate risks associated with firewall failures.
Implementing UTM Firewalls: Best Practices
Successful implementation of UTM firewalls involves:
- Planning and Assessment: Conduct a thorough assessment of network requirements and potential risks.
- Proper Configuration and Deployment: Ensure correct setup to maximize security effectiveness.
- Regular Updates and Maintenance: Keep the firewall updated with the latest security patches.
- Monitoring and Incident Response: Continuously monitor network traffic and have a plan for incident response.
Future Trends in UTM Firewalls
The future of UTM firewalls will see greater integration with AI and machine learning, enhancing threat detection and response capabilities. There will be an increased focus on cloud security as more enterprises adopt cloud solutions. Additionally, evolving threat landscapes will drive the development of more sophisticated security measures.
FAQs about UTM Firewalls
- What is the difference between UTM and Next-Generation Firewalls (NGFW)? A: NGFWs offer more advanced features and better performance, while UTM provides a broader range of integrated security functions.
- Can UTM Firewalls replace all other security tools? A: No, they complement other security measures but cannot entirely replace specialized tools.
- How often should UTM Firewalls be updated? A: Regular updates are crucial, typically every few weeks, or as new threats emerge.
Conclusion
In summary, UTM firewalls play a pivotal role in modern network security. It is offering a comprehensive and integrated approach to threat management. Staying updated with the latest security solutions is essential for protecting enterprise IT infrastructure. As cyber threats continue to evolve, UTM firewalls will remain a key component in safeguarding digital assets and ensuring robust cybersecurity.